Spotting Fraud: What to look for
Every day, whether at work or at home, we receive emails that, on first glance, may look harmless, but upon further review, contain common phishing red flags. Below is a breakdown of each component of a standard email, including questions to consider and red flags to look for before selecting a link, opening an attachment, or responding to an unsolicited email.
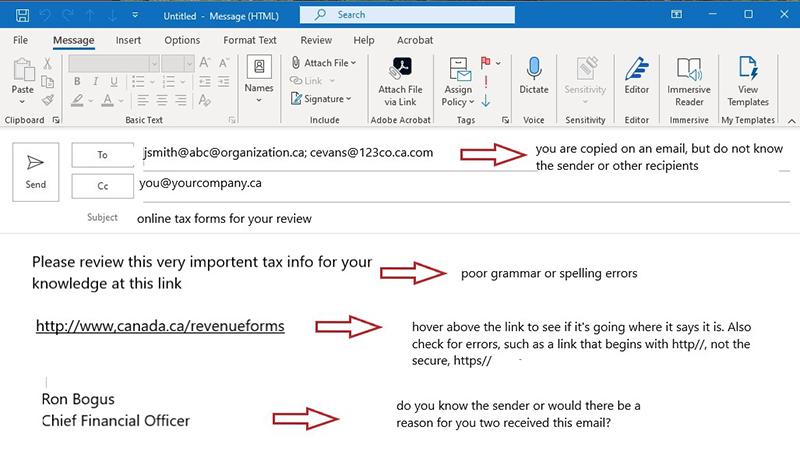
- Why are they sending you this email? Do you know or recognize the name or email address of the sender?
- Even if the email comes addressed to you and contains personal information, it still may not be legitimate, as this is a common tactic used by scammers to earn your trust. It’s better to focus on who is sending the message, rather than the personal details included in the message.
- You don’t know the sender personally nor has anyone vouched for them.
- The email is from someone outside of your organization but is unrelated to your role in the company.
- The email is from someone inside the organization, or a vendor but is unusual or out of character for you to receive an email from them. Instead, contact the sender directly to confirm they sent the email, and inform your IT department about your suspicions.
- Is the sender’s email address suspect, or from a suspicious or unfamiliar domain?
- Is this an unexpected or an unusual email from someone that you haven’t had contact with for a while that has hyperlinks or attachments?
- You are cc’d on an email, but you do not know any of the other people or the organizations on the list.
- You are cc’d on an email that contains a curious combination of other people.
- The email did not come at a regular time of day, or came at an usual time, such as receiving a work-related email at 3:00 a.m.
- The subject line has nothing to do with the content of the email.
- The email is a reply to an email that you never sent.
- The attachment is unrelated to the subject of the email, or it was unexpected.
- The attached file is a file type you’re unfamiliar with or seems suspicious.
- When you hover over the website link in the email, the link-to address is a different website than what is displayed.
- The email contains a single long website address with no other content in the email.
- The hyperlink in the email contains a familiar looking address but contains spelling errors or an additional letter.
- Never use any links in an email to access your banking. Only access your online banking from our website or mobile app. SCU will never ask you to select a link to access your account or to contact us.
- Be suspicious of links in emails from the CRA, Microsoft, credit cards, or similar password protected access. Type the website address directly into your browser so you can confirm that it is safe.
- Is this email asking you to open a link or an attachment to avoid a negative outcome?
- Is the email unusual or does it contain spelling, text, and grammatical errors?
- Does the email come from an incorrect, but similar email address of a close contact, but contains unusual content or lots of errors?
- Does the request seem peculiar or is the email asking you to open an attachment or to select a link with no reason?
- Is the email requesting you look at threatening or compromising information of you, or someone you know?
- Is urgent or threatening language used in the email?
- Is this an unsolicited email claiming an account closure, money owing, or requiring immediate action?
- Is the email asking you to share sensitive/personal information?
- Is there a logo in the email signature? Legitimate businesses often have logos, or a company email signaturee. Unprofessional design in an email signature can include a blurry logo, lack of formatting or no email signature at all. This is a red flag that an email is coming from an illegitimate source.
Text message fraud
SMS Phishing (or Smishing): Phishing attacks, which are misleading emails or text messages designed to trick you into clicking on a malicious link, account for more than 80% of reported security incidents.
Never download attachments or click on text links that come from people or phone numbers you don’t recognize.
Online fraud
The internet is both a blessing and a curse. The benefits are countless, but as we’ve learned — so are some of the unforeseen consequences. Here are some tips to protect yourself.
- Remember to protect yourself while online by:
○ Updating your browser with the latest version. Many have built-in protection against fake sites and viruses.
○ Getting the latest anti-virus or firewall software to protect you against online hazards.
○ Whenever possible, use a VPN when using public networks to protect yourself and never conduct online or mobile banking on public Wi-Fi. - Online advertising fraud has been relatively easy and lucrative for fraudsters, difficult for online ad platforms to control, and a financial burden for victims and legitimate advertisers. The majority of internet fraud occurs through computer viruses that open the computer to scammers.
- Look for a "lock" icon at the bottom of your browser and make sure "https://" appears in front of the Web address before submitting any personal or financial information through a web site. If these are not part of the address, this is a red flag. These visual clues tell you the information you are sending is secure.
- Look out for sensational headlines or shocking images that are click-bait and intended to lead you to dangerous websites and to take unnecessary risks.
- Remember, regardless of how you receive the offer, if it sounds too good to be true. It probably is. A good thing to remember is that your chances of winning the lottery are slim, but it's impossible to win a lottery or prize that you did not enter. This is also a red flag for search engine phishing, which is when a website is created that offers cheap products or amazing deals to get it indexed by legitimate search engines appearing in the top of search engine result and easily accessible.
- Verify links before clicking on them by hovering your mouse over the link and carefully checking that it's the website that you expect. The difference may be as simple as a .net address versus a .com address, or a slight difference in spelling, so pay close attention.
- Be skeptical of websites containing misspelled common words; grammar errors or misused common expressions that make the website difficult to understand (similar to emails and texts).
- Do not go to sites from links you have received through an email, text, or an advertisement. Google Ads show the destination website address near the ad headline. Hover above the link to confirm it is what you expect before clicking, and if unsure, don't click the link.
- Go to the source directly and type in the company website yourself to verify and use the information from the website.
- Do not click on pop-up ads when browsing online. Using anti-virus software should help you avoid these dangerous diversions.

Fraud terms
A whole new vocabulary has been created to describe the many methods scam and fraud artists’ use to deceive and trick people into responding with risky behaviour. You can review a list of common banking terms from our website glossary, including those phrases commonly used in fraud.
Explore our fraud glossary